What Is DDoS and Was An Attack Launch At The EOS Network
bitcoin·@aclarkuk82·
0.000 HBDWhat Is DDoS and Was An Attack Launch At The EOS Network
---  --- ### Preface </br> I will not be providing an exhaustive or highly detailed description of DDoS attacks, that is far to complex to cover in a single post. Engineers spend years learning the patterns and types of attacks and in return, earn very sexy salaries. I would like to open discussions and inform people so when we hear messages such as > Blockchain x is being DDoS'd We can reply with confidence. ### Technical Definition </br> </br> >A distributed denial-of-service (DDoS) attack is an attack in which multiple compromised computer systems attack a target, such as a server, website or other network resource, and cause a denial of service for users of the targeted resource. The flood of incoming messages, connection requests or malformed packets to the target system forces it to slow down or even crash and shut down, thereby denying service to legitimate users or systems. <center> Quote source </center>https://searchsecurity.techtarget.com/definition/distributed-denial-of-service-attack </center> The above is saying a DDoS attack is the distributed version of a DoS (Denial of Service) attack. A DoS attack tries to exhaust the resources used by the victim host, be it memory, CPU cycles, max web sockets connections (classic one for Windows servers running IIS) or even allocated bandwidth, also known as, the CIR ( Committed Information Rate). Distributed in this context means that the source of the 'attack' traffic will be distributed between many different servers, PC's, smart devices (including light bulbs) and not from a single host. Effective DDoS attacks also use geographically diverse sources which makes it a little harder to stop in some cases as I will try to explain later. Using a distributed model makes it a lot easier for the attacker to inflict the damage intended exponentially faster while allowing the assault to fly under the radar of the incognizant attacking systems. An assailant will need to 'collect' zombie machines of their own or rent what is known as a 'botnet' from someone else to launch the attack. Using these collections of unaware accomplices, usually gathered via malware ( thanks online porn industry), each node in the botnet will not need to use many resources if the total number of infected hosts is large, keeping the users attacking another system in the dark, sneaky heh. Generally are three main types of DDoS attacks that we see, (or at least I have seen in my career ). These are * Network-centric or volumetric attacks. * Protocol attack at layer 3 or 4 of the OSI model. * Application layer attacks ### Botnets As mentioned above, botnets are the gather of compromised systems really to do the bidding of the owner. The typical communication structure of a botnet is the "Command & Control" mechanism in which the zombie systems all connect to a central location via the old skool chat protocol called IRC (Internet Relay Chat). From these rooms, the owner of the botnet could issue a command such as "Attack IP 1.1.1.1" and all the systems connected would launch a pre-defined attack method towards the destination IP of 1.1.1.1. Here is an example of a botnet layout: ---- <center>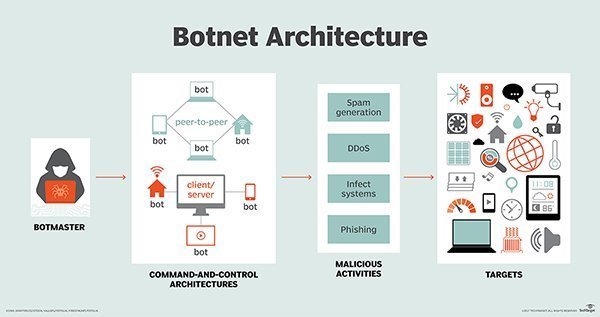</center> <center>Image source</center><center>https://searchsecurity.techtarget.com/definition/botnet</center> ### The Incentives </br> The launch of the EOS network, entailed the term DDoS being thrown around when it came to bringing the system online. A DDoS attack against an EOS block producer was and still is a real and present danger, especially among the block producer community themselves. Even though the EOS network has only been live and active for a few days (minus the few hours they went down due to the bug), the payout's for the top 21 block producers quite lucrative already as you can see from the table below: 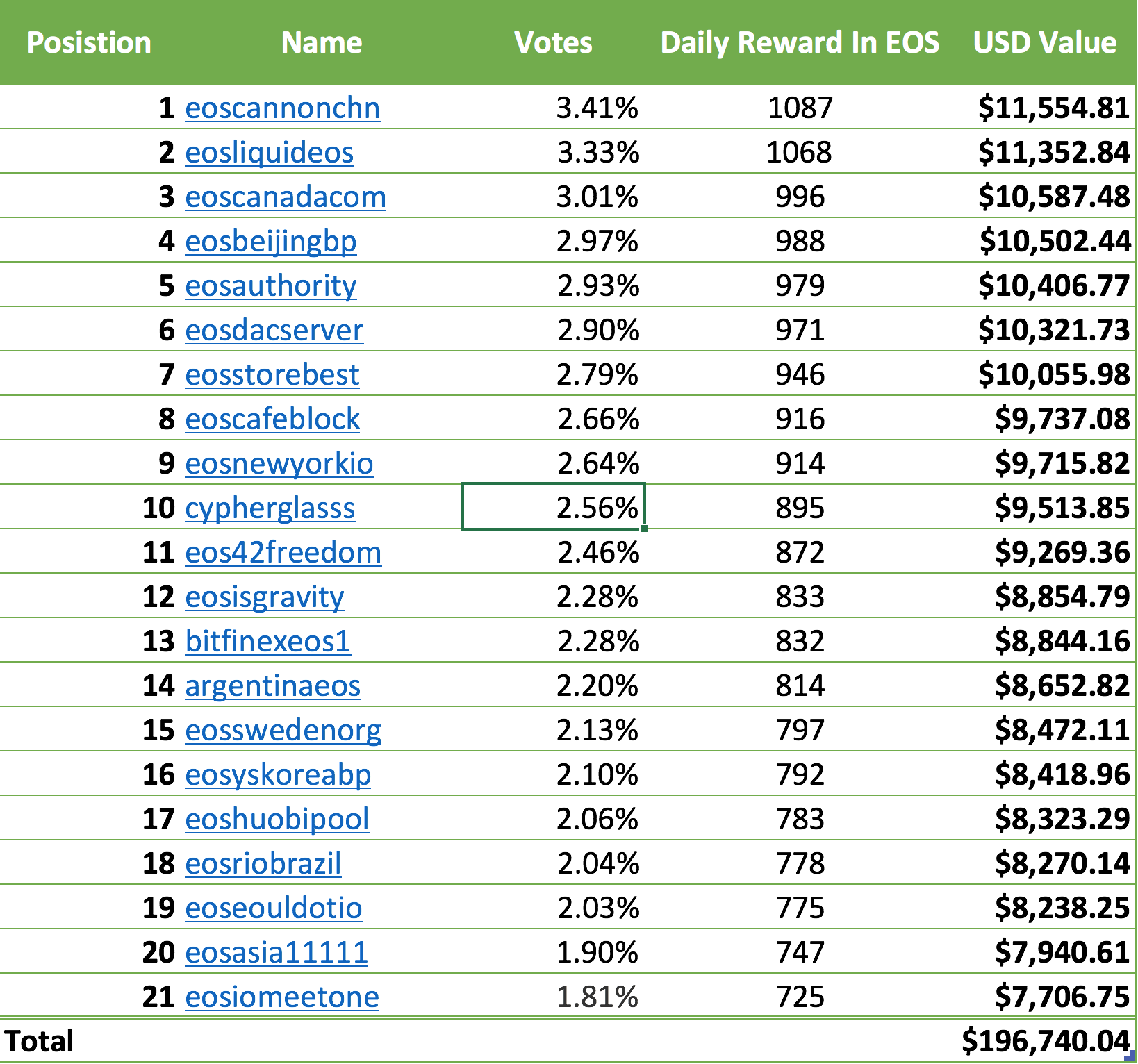 Moreover, even backup block producers should not crumble as they too have made a good wad with zero effort. So the temptation to knock one of your frenemies off the network using a DDoS attack is most certainly a financial temptation. The fear of DDoS during the launch was that an attacker would target a block producers infrastructure, thereby taking down their ability to communicate with the other block producers which would have stalled the start of the mainnet. I have been looking into the infrastructure documentation and diagrams, most of the serious candidates have subscribed to DDoS mitigation services will 'cleanse' malicious traffic while allowing legitimate traffic to pass. ### Was EOS DDoS'd </br> The short answer is no?. Let's look at what facts were going around the various social networks; this image seemed to be the most popular. 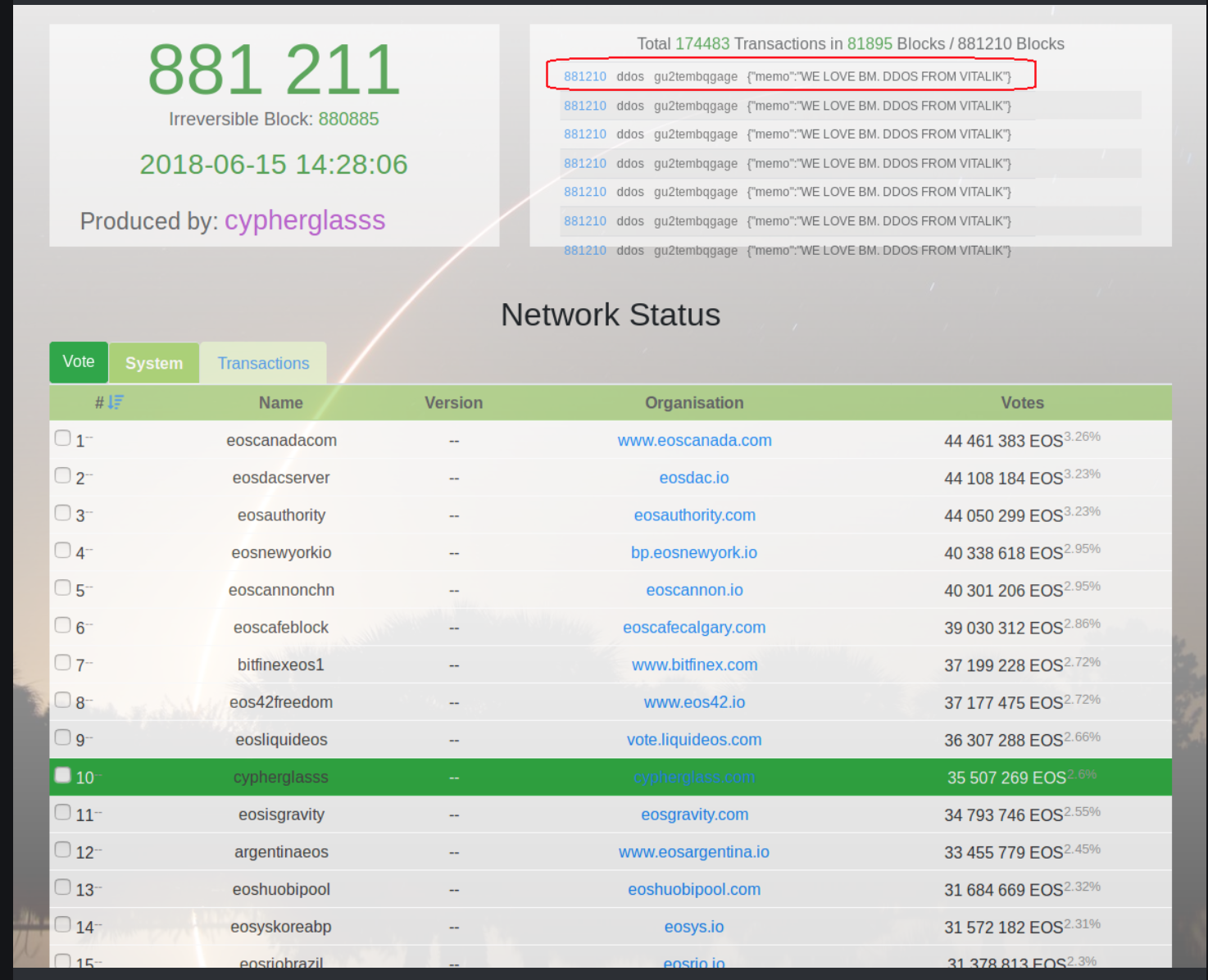 The image shows one account sending transactions across the network which they are completely entitled to do. Moreover, this is a single account so by definition, this is not a DDoS, so maybe this could be a DoS attempt. If this was a DoS empty it was weak, here is why. When we look up that username, that person has so few tokens that the network will not even feel their presence. They will also use up there bandwidth very quickly; moreover, the system is designed to respond rapidly to a single account filling consecutive blocks, throttling their virtual bandwidth and slowly ramping it back up over 10 minutes (1% increases). Not even an account with 10% of all tokens could make a big impact on the entire throughout. So no, this was not a DDoS attack, nor was it an attack, it if was the person is woefully inept, so relax all.
👍 aclarkuk82, grammarnazi, x33, hr1, submitchair, steemitboard, bubke, iotdevnet, questingtw, dragon40, zikaa, badham, vintherinvest, ran-a-banana, initforthemoney, meansteemachine, avesomejuni, dheerajdj, mawit07, cryptomoneymade, showmovie, yuemay, grizzle, jansher, darkcyderails, daviddivergent, loudlou, sugarfix,