FUNCTION X: POWERING A NEW DYNAMISM OF BLOCKCHAIN ENHANCED INTERNET SERVICE
blockchain·@anderhart·
0.000 HBDFUNCTION X: POWERING A NEW DYNAMISM OF BLOCKCHAIN ENHANCED INTERNET SERVICE
OVERVIEW: The Internet has become an integral part of human nowadays as we cannot do without it for some minutes. This internet is seen as a means of getting news as numerous communication stations now use the internet as a means of news dissemination. In the same vane, a lot of people now do countless online business ragging from trading to digital asset, and so on. Some services are as well rendered on the internet while internets is now one of the best places to get your markets advertised as there are thousands of people who assess the internet per minute. As great and benefiting this internet is, there exist some transparency and security problems as people data usually get hacked and broadcasted. In a countless number of times, accounts were illegally assessed, used to send messages and even spread the sensitive information to generate traffic and earn more money. To discontinue this unscrupulous act function x is created. SHORT CHRONICLES OF FUNCTION X  Function X is an architecture which is made for the creation of the needed decentralization procedure that is needed by the internet for maximum security and transparency of internet users. It has become obvious that the mediums that are built on blockchain technology are already very safe and transactions are openly done. This is why the function x introduced it to the internet as the only measure needed to correct these issues in a time like this. This architecture is having the acronym f(x). The team behind the f (x) creation discovers the need to introduce blockchain to the global telephony, storage, and data transmission industry. That was why they quickly do to stop those menaces that befall users of the internet. THE COMPONENT THAT ENHANCES A SUCCESSFUL DECENTRALISED INTERNET SERVICE OF FUNCTION X .png) The architecture that was developed is not only a public chain but architecture with a total solution. For the effectiveness of this blockchain solution, the following components are integrated into the architecture; * Function X Operating System 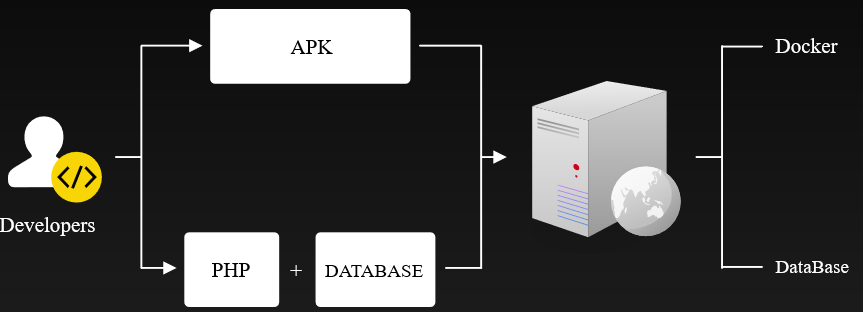.png) The reason for this is for the component to give room for IoTs and smart hardware to support the potential and effective utility of the decentralized techniques. The architecture has developed an in-house solution for the way a mobile phone will easily utilize Function X like as it is in the XPhone. This Operating system can also be adopted by other companies that will have it customized to function in their device as well. * The Ecosystem Function X This component is tagged Function X FXTP Protocol. With this protocol, data transmission functions using the public exchange that is complex but does not pass through any intermediary. The data that pass through f(x) are encrypted and secure using private key through this FXTP protocol. This allows communication free from interception and provides the opportunity for users to directly share their data as they wanted. * Function X Blockchain The Function X blockchain is put in place for transaction running. It serves as a base for all the architecture transactions. * F(x) Chain This component incorporated with f (x) ecosystem and it is the architecture consensus algorithm which took the nature of the distributed ledger. This chain alongside the f(x) blockchain that is the ledger building block, help in the keeping and verification of transactions. Examples of such transaction are payment transaction, financial transactions, communication-related transactions like phone calls, storage, file transfer, Service-related transactions like creation or utilization Decentralised app among others. Function X IPFS This component is also a protocol and a network that is responsible for the storing of data on the distributed system. When any user needs to carry out file retrieval, such user will call the file identifier tagged hash. Once this is done, this protocol will search through other nodes so that the file can be supplied. The files are safety kept on the IPFS protocol. In case of users having personal nodes, the files of such users are only kept in their node and downloadable on the permission of the user. Are you tired of the current internet security threat? why not try out Function X architecture today, and be glad you did. .png) To get further insight about the project, please click on the links below: Website: https://functionx.io/#/ Facebook: https://www.facebook.com/FunctionX.io/ Twitter: https://twitter.com/functionx_io Concept paper: https://functionx.io/assets/file/Function_X_Concept_Paper_v2.0.pdf Telegram: https://t.me/functionx YouTube: https://www.youtube.com/channel/UCmS83bWNR43jwEOC6EJaOyw ANN thread: https://bitcointalk.org/index.php?topic=5166702.0 Author's Bitcointalk Username: Jannyh Bitcointalk Profile Link: https://bitcointalk.org/index.php?action=profile;u=1883625 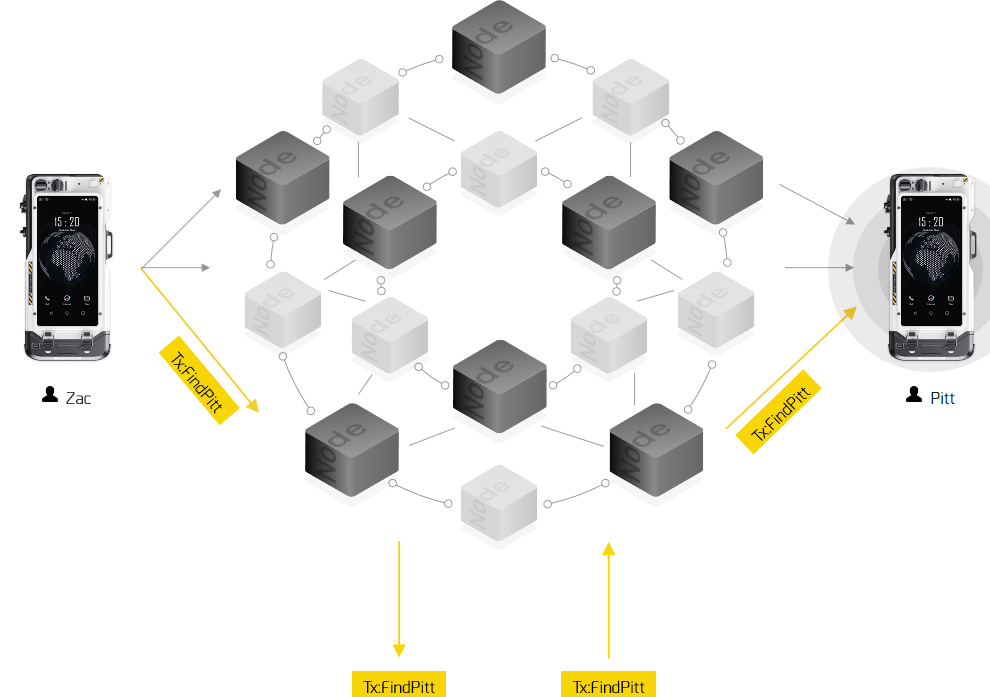.png)
👍 stevenomole, dulowegner, depedro, emmy92, temmyjen, unfredo, royalt123, clektai, miracle24, ebykamsiokoro, phlaser, elmichaels, empress01, deodivine, hush231, tcode53, phylum, crystaljonah1, smartzboy, ifabre, oniraphaeleu, leoxina, prinxeton, mexite, lekato, dellosoft, cryptoboss12, supzeel, buchito, chike4545, mrlong007, aflozy, investokay, emilanoh, dessyhodin97, aakay, tbossmitche, aaaapraise, trishacole, aaacherry, bigjoe4114, idakpe, nsiman, ajaxkennes, ibrash600, oluwatosin10, olamidey, walexworld, honpaulo, xratedx, aaatriplechief, damkem, darekem, highest01, chudidonas, aaamidastouch, akeyboardwarrior, abdulbc, chuks0chuks, atteh, aaemma, macanselm, aaarezy, anosend, johnsule, lachious, nebuachampor, akpalilu, kamogtechs, tivere, kimblycara, alynks, jivwe, aaaxpress, unekwu90, tesmo, bosunbossman, assured, ritabella, swingle, rylnei, bellaross, boomeranggg, funex1, kpelumo, mickeyberry, sprintx24, annylex, kessypatty, aaaaachy, haleeberri234, knowels, modanalee, punamidin, limitlesschuks, elynks, hypergrace, deeshawn, soludo, debbbi, styxfury, wayne5, aaaalek, oguybobo, idokometu, hothenry, smarthenry, minstrel, jennyexcel, funmi24, lapstick, devinlex, kalimba, sadeller, johnexboi, lizzysneh, ifeoluwa358, romanbankz, benbrucz, ufyandrew, ivankadon, osasu, confy0065, hunterwayne, kylebrownz, satoshikid, umuoji, rucky, chacha10, makdon, ibori, gemboy, vowhe, sassee, chikky08, cryptovipa, certifiedgee, russeme, rosarymay, juzcrypto, afloxy, okowa, wike, coinaddict, adebits, omogold, nedbee, mack-bot, jdion, mbaisechick,