SCIENCE OF HIDING THE EXISTENCE OF DATA IN A COVER OBJECT
steemstem·@noble-noah·
0.000 HBDSCIENCE OF HIDING THE EXISTENCE OF DATA IN A COVER OBJECT
Trillions of data is being transferred daily, from one system to another system, either through the secondary storage device like Flash Drive, CD-ROMs or on the web server or on a peer to peer network and thus there is highly need to improve the security and safety of this data. <center></center> <center>[credit](http://www.e-cycle.com/wp-content/uploads/2011/09/data-security.jpg)</center> In **Cryptography techniques**, which the **cryptocurrency** and other **blockchain** applications was built on, the encrypted data is transferred after the data is changed totally to another form in other to protect the content of the data from unauthorized users. While Cryptography is working well for the purpose it was built for, the quest to improve on this security lead to **Steganography**, this deals with protecting the presence of the data using a cover object such as image, texts, audio/video and protocol rather than changing the data itself, this technique cut people unaware that information is being passed from one system to another. **Brief Overview of Ancient Steganography** The history of Steganography can be linked to ancient times when chemicals and even human bodies were used to convey information. Today’s advance in Information and Communication Technology has advanced beyond the use of chemicals and physical human bodies, but in principle, it can still be referred to as the same as the ancient steganography. Some of the histories are outlined below: <center></center><center>[credit](https://www.dreamstime.com/stock-image-herodotus-statue-image26776381)</center> **Herodotus (484 BC – 425BC)** was one of the earliest Greek historian. His great Work, The Histories, is the story of the war between the huge Persian Empire and the much smaller Greek city–states. Herodotus was known for telling and reporting stories, some of his stories are fanciful and some inaccurate, though he explained that he is only reporting what he was told: he reported that when Histaiaeus wanted to persuade Aristagoras of Miletus to revolt against the Persian King in other to secure convey his plan, Histaiateus completely shaved the head of one of his trusted messenger, he then wrote the information on his scalp and waited for the hair to regrow. The messenger, apparently carrying nothing contentious, he could travel freely without anyone noticing him, when he arrived at his destination, he then shaved his head and showed it to the recipient to read. <center>[credit](https://www.thefamouspeople.com/profiles/pliny-the-elder-31965.php)</center> **Pliny the Elder (23 AD – 79 AD)** narrated how the thithymallus plant’s milk dried to transparency when it was applied to paper and darkened to brown when it urdergo heating, this can be linked to recording one of the earliest recipes for invisible ink. An ancient chinese wrote small notes on a small silk which was wadded into little balls and coated in wax, which is to be chewed by a servant and retrieved back at the servant’s gastro-intestinal convenience.  <center>[credit](http://iniziazioneantica.altervista.org/1500-1600/della_porta/giovan_b_della_porta.htm)</center> **Giovanni Batista Porta (1535 - 1615)** explained at length, how to conceal an information within a hardboiled egg by writing on the shell with an ounce of alum and a pint of vinegar. The solution entered through the porous shell, leaving no visible trace, though the message is stained on the surface of the hardened egg albumen, so it can be seen when the shell is removed **MODERN STEGANOGRAPHY** Image steganography can be implemented using both Spatial domain and Transfer domain, which implements any of these three methods: **Non-Filtering**: This method deals with embedding the data directly into the cover object(image, text or audio/video) by initializing and replacing the cover object bit, i.e. from the first pixel of the images to be used as cover object. **Randomized**: In this technique, both the receiver and sender make use of the password denominated called 'stego-key', this is employed as the seed for pseudo random number generator and later creates series that is used as index to have right access to the corresponding pixel. **Filtering**: The algorithm filters the cover image by using a default filter and hides the message/information in the areas that get a better rate **Steganography Algorithms** Research has shown that many algorithms that work in Spatial Domain use the so called ‘Least Significant Bits Algorithm (LSB)’ techniques or any of its kinds as the algorithm for information hiding. This hides one binary digit of message to hide in the least significant bit of each color of a pixel of a cover object (image). This method works well, but the method cannot stand some types of statistical analysis. The problem arises from the fact that least significant bit modifies the three colors of a pixel, which later produces a major distortion in the resulting color of the cover object (image). This distortion is certainly not visible to ordinary eye, but detectable by statistical analysis. Research has also proved that the methods that work in the spatial domain is faster and simpler to implement than the one that work in the transform domain which is more robust in term of resistant to attacks. **Least Significant Bit Algorithm** Hiding data using Least Significant Bit Algorithm: The message to hide and the cover object to use must firstly be converted from their various pixel format to binary representatives, after this must have taken placed, the Least Significant Bit of the cover object, which can be text or image which must then be substituted with the bit of the message to hide its existence. The bits of the message replaces each of the colors of the Least Significant Bit of the cover object, which can be Image or text. For instance, suppose I want to hide the existence of my steemit pin ‘AID’ in a cover object (image). Before I explain further, you must know that everything that appear on a computer screen, including this text you are reading, is represented as an image. An image can be defined as an array of values called pixel. Pixel consist of three colors/channels (RED, BLUE GREEN), each of this color has 8 bits. Now, to hide ‘AID’ in a cover object, let say one of our images. The process will follow thus: 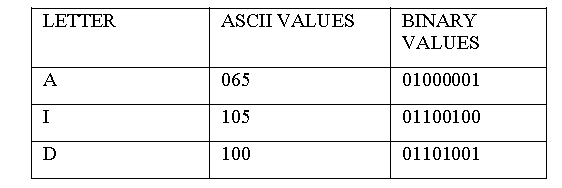 To hide my steemit pin ‘AID’ with the Binary Code (01000001 01100100 01101001) as shown in the diagram above using Least Significant Bit Algorithm, each bit with the least significant(lsb) bit of each color that made up the pixel is flipped. The affected bits is 1/2 of the bits of the cover object used here(image), since there are almost 256 possible intensities of each primary color, changing the lsb of a pixel results in small changes in the intensity of the resulting colors. These changes cannot be perceived by the naked eye and this cuts the people unaware of the existence of the pin. **Selected Least Significant Bit Algorithm** In Selected Least Significant Bit Algorithm, the message to hide and the image used as cover object are both converted from their pixel format to equivalents binary. The Least Significant Bit of one channel/colour, i.e. (BLUE) that made up a Pixel is substituted with the bit of the data/message to hide. Only the Least Significant Bit of one colour in a Pixel is flipped through by the bits of the message/data to hide . Only one-third (1/3) of the bits of the image is used. Hiding Data using Selected Least Significant Bit uses more pixels of images as against the Least Significant Bits, this is due to the fact that only the last color of the Least Significant Bit is going to be displaced. In this technique, the human eye cannot perceive the changes and this makes the message to be successfully hidden and cut the awareness to the human eye. Note: In this research work, I only considered image as the cover object. Other forms of cover object like text, audio/video follow similar technique. References 1. [Steganography- A Data Hiding Technique](http://www.ijcaonline.org/archives/volume149/number3/25974-2016911363) 2. [A Modified Side Match Scheme for Image Steganography](https://pdfs.semanticscholar.org/3ea3/5c93462c3be0b3284cddc419166507abc664.pdf) 3. [Hiding a large amount of data with high security using steganography algorithm](http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.97.1453&rep=rep1&type=pdf) 4. [A Survey on Various Encryption Techniques](http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.648.6040&rep=rep1&type=pdf) 5. [A steganographic method for images by pixel-value differencing](http://www.asia.edu.tw/Main_pages/about/Former_president_TsaiWH_publications/Journal%20Paper%20PDFs/Wu_%26_Tsai_PRL_2003.pdf) 6. [Herodotus](https://www.dreamstime.com/stock-image-herodotus-statue-image26776381) 7. [pliny-the-elder](https://www.thefamouspeople.com/profiles/pliny-the-elder-31965.php) 8. [Giovanni Batista Porta](http://iniziazioneantica.altervista.org/1500-1600/della_porta/giovan_b_della_porta.htm) 9. [An overview of image steganography](http://icsa.cs.up.ac.za/issa/2005/Proceedings/Full/098_Article.pdf) 10. [Enhancing the Least Significant Bit (LSB) Algorithm for Steganography](http://www.ijcaonline.org/archives/volume149/number3/25974-2016911363) 11. [Implementing Steganographic Algorithms: An Analysis and Comparison of Data Saturation](http://starshine.org/xteddy/thomas/~n6tadam/project_proposal.pdf) Thanks for reading through and hope I have contributed to the knowledge domain. Your thoughts are very important! <center>https://thumbs.gfycat.com/PowerlessHastyAmericanbittern-size_restricted.gif<center> <center>@steemstem animation by the great @foundation</center>
👍 ojaber, bue, sammy111100, noble-noah, steemstem, anarchyhasnogods, lemouth, justtryme90, dna-replication, curie, mobbs, the-devil, locikll, ewuoso, sammarkjames, jasimg, xanderslee, anwenbaumeister, markangeltrueman, howtostartablog, ivan.atman, hendrikdegrote, foundation, lamouthe, ajaxalot, tensor, slickhustler007, rachelsmantra, nitesh9, kushed, gra, rjbauer85, amavi, dber, gentleshaid, mystifact, hadji, fredrikaa, abigail-dantes, ertwro, steemulator, gohba.handcrafts, steemstem-bot, steemitboard, rok-sivante, ovij, oluwabori,