[TUTORIAL] Basic Computer Security [5]
technology·@profitgenerator·
0.000 HBD[TUTORIAL] Basic Computer Security [5]
<center> </center> <br/> A few more things came to my mind so let me make another quick post. I still haven't finished the part about the kernel security because really that is the most important part. Apps and userspace security is trivial, but it always goes back to the kernel. If the kernel is exposed then the entire system is compromized. So it has to be protected massively. **Here are the previous parts, make sure your read them all if you want to stay up to date:** * **1) [Hardware Selection & Proper Usage 1](https://steemit.com/technology/@profitgenerator/tutorial-basic-computer-security-1)** * **2) [Hardware Selection & Proper Usage 2](https://steemit.com/technology/@profitgenerator/tutorial-basic-computer-security-2)** * **3) [Kernel Defense 1](https://steemit.com/technology/@profitgenerator/tutorial-basic-computer-security-3)** * **4) [Kernel Defense 2](https://steemit.com/technology/@profitgenerator/tutorial-basic-computer-security-4)** Okay so in the previous part I have discussed a strategy of "boxing" malware inside a Virtual Machine so that it will be kept quarantined from the Kernel, and of course several VM's used for compartimentalization between sensitive work and casual work. Now that is all cool, and you can really setup your computing experience that way, but it will probably be hard for a novice and in fact there is an even easier way and in fact safer way to do it. It's not just that setting up Virtual Boxes is hard for a newbie, but it's also very uncomfortable to work that way, and in fact in may not even be as secure as you think. <BR/> # Problem with VM Setup Don't get me wrong it's infinitely more secure than what you are using now, but it's still not an ultimate setup. Since the VM software itself is just too complex and it's GUI so it has to rely on [QT](https://www.qt.io/) and many other packages, and we know that the more complex something is the more prone it is to undiscovered bugs. So why complicate it? What if there were a system that would both be ridiculously easy to use (even for Linux newbies) and also much more secure, and it would also eliminate the human error (of messing things up), since the compartimentalization and the VM destruction is already configured for use.... ? Well there is, it's called QUBES. <br/><br/> <CENTER></CENTER> <CENTER><H1>[Qubes](https://www.qubes-os.org/)</H1></CENTER> Qubes is like a dream come true for a security enthusiast. Everything that [I described in episode 4](https://steemit.com/technology/@profitgenerator/tutorial-basic-computer-security-4) can be done in Qubes, much more easily and literally pre-configured so it's just a couple of clicks for people. Qubes is an operating system built for compartimentalization and virtualization of computing activities. So there is really no reason to do what I described in episode 4, just install Qubes only and everything you need is built into it. Qubes is running something called a hypervisor performed by [Xen](https://en.wikipedia.org/wiki/Xen) which would be the equivalent of VirtualBox, but instead it runs in the kernel, and I think it's probably better hardened and more safe than VirtualBox. **The hierarchy inside the Qubes environment is like this:** <CENTER>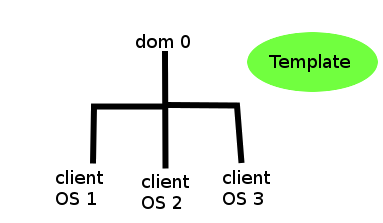</CENTER> So you have the “Main OS” as described in the previous episode, but here it’s called `dom0` for some reason. It’s the Main OS part that can only be used for administrator maintenance, updating the kernel and things like that. I don’t think it even allows to install any additional software here. Then you have a Template (Fedora,Debian & Whonix), so you can use this to restore or create new VM from this template. Also the template can’t be used, but only updated I think, so this removes any possibility of a malware compromizing it (not to mention it probably already is linked to trusted repos with a GPG key, so only signed updates can be downloaded & installed by default). And then you can create as many client OS’s as you want from the Template. You have a Fedora, a Debian and a Whonix OS as a template but I think other ones can be installed too. So a Fedora can be setup in like 2 minutes and then that can be used as an OS for a certain activity. Fedora is like a casual OS, while Debian is for security (since it’s fully open source) and Whonix is a privacy oriented distro. So you can choose which one you want to use, and again others can be installed too, but it needs additional configuration. <br/> **The basic features are that:** * Guest OS’s I think can’t communicate between eachother, so your Banking OS and your Porn OS is totally separated. However information can be sent over, but through a hardened channel controlled by `dom0` which is allegedly totally safe as much as Xen can provide, but only with the authorization of the `dom0`, so rogue elements inside can’t leak out. * The `dom0` I think can insert files into a Guest OS, but a Guest OS can’t communicate directly with the dom0 without it’s authorization. * There is a possibility to create a non-networked OS, for cold storage. * There is a possibility to create an anonymous OS where the internet is routed through a [VPN](https://steemit.com/privacy/@profitgenerator/best-vpn-list-guaranteed) or [Tor](https://torproject.org/). * There is a possibility to create a micro OS that can be destroyed even after 1 operation (so like opening an untrustworthy .PDF file, reading it, and then closing it, and self-destructing the VM with it) And despite how complicated it would sound, it’s literally very easy to use that even your grandpa can use it. It’s all GUI so even your Linux novice can use it, although console experience might be required for updating and management of the system. I have tried and downloaded Qubes about a week ago and it’s pretty easy to use, but I only use it on my other computer, I usually keep this one for casual stuff. It was very easy for me to get used to it, so I really can recommend it to everyone who wants security. But install it in a different computer as a clean install, [DUAL BOOT](https://en.wikipedia.org/wiki/Multi_boot) IS NOT RECOMMENDED EVER! **It looks like this:** <center>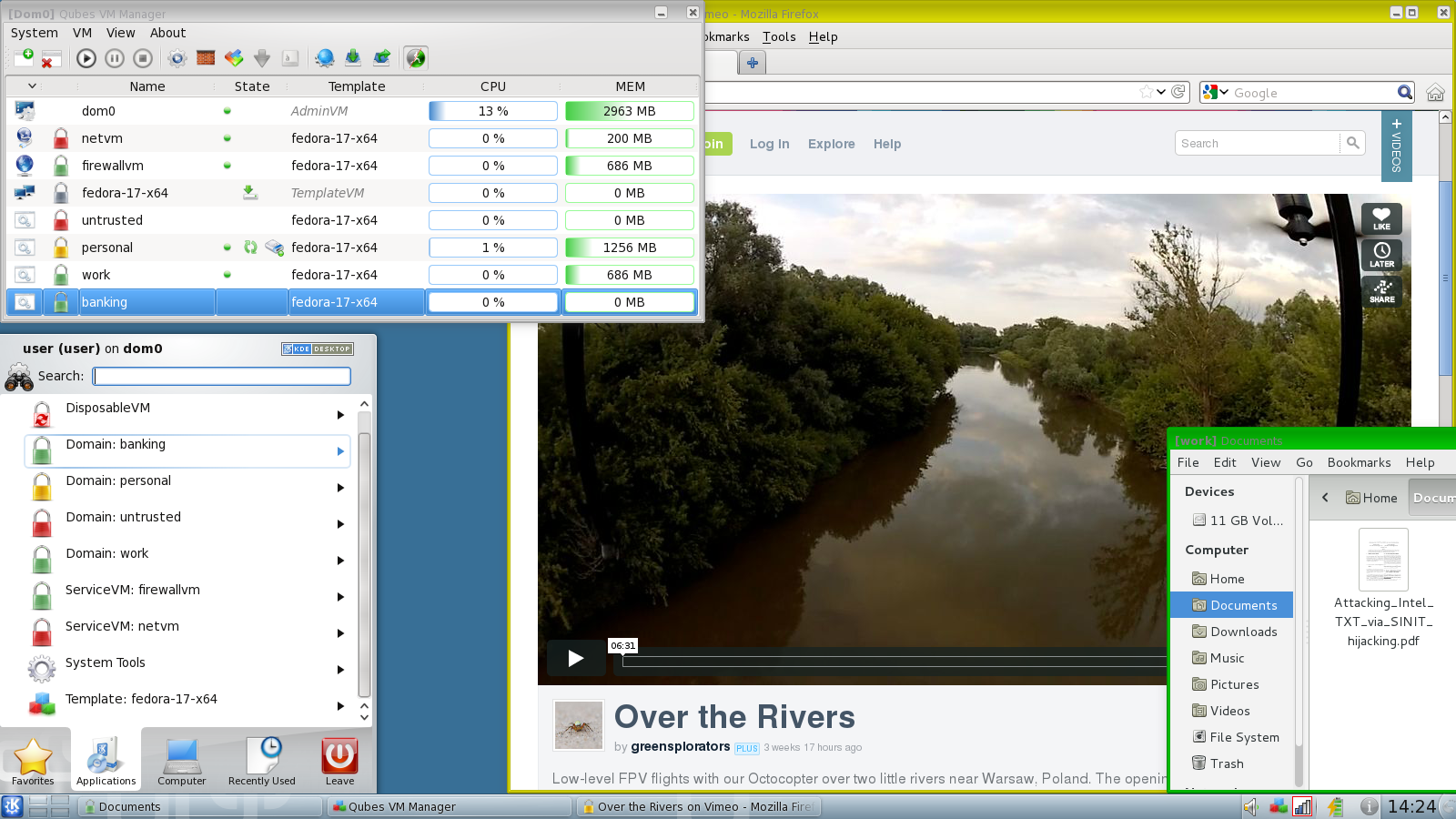 <sup>By Brunogabuzomeu [GFDL](http://www.gnu.org/copyleft/fdl.html) or [CC BY-SA 3.0](https://creativecommons.org/licenses/by-sa/3.0), via Wikimedia Commons</sup></center> As you can see in the picture above a yellow color coded VM was opened (you can basically set it to any color you want, to differentiate between workspaces) which corresponds there to “Personal”, so this particular VM would be for example handling photos of yourself or your family that you don’t want to mix or taint with malware or even spyware from other softwares. Like for example [VAC](https://en.wikipedia.org/wiki/Valve_Anti-Cheat) is allegedly a spyware that has been reported by many to be too invasive, allegedly scanning through files on people’s computers, watching out for running softwares, logging IP history and things like that: * https://www.reddit.com/r/privacy/comments/1y0btj/rumor_valves_anticheat_vac_allegedly_snoops_your/ * https://www.reddit.com/r/privacy/comments/721cql/when_malware_gathers_large_swaths_of_information/ So if people think that they don’t want any kind of software that would have the capacity to spy on files to have access to their personal photos and videos, then quarantining that user space against potential apps that would do that would be a smart move. You can even run Windows inside a VM inside Qubes, so you can totally play all games or whatever that you would need on Windows, but isolate everything else that is really important from it. So all the security benefits as suggested in episode 4, and even more, and none of the drawbacks from that system. With Qubes you can have the entire compartimentalization system on 1 DVD. In fact it’s even safer since you can verify the DVD afterwards and the downloaded .iso, so you don’t have to rely on downloading everything by yourself. Just 1 .iso file, that’s it. <br/><br/> <CENTER><H1>Get Qubes</H1></CENTER> ### 1) Download the latest Qubes from here: * https://www.qubes-os.org/downloads ### 2) Verify that the website is HTTPS, cerfified via `COMODO CA Limited` ### 3) Verify the HTTPS certificate SHA256 fingerprint: `0A:E2:2E:D9:8E:54:F8:7A:E1:D8:34:3D:60:F3:62:08:EA:73:17:62:59:7C:CD:67:1E:A3:EC:E6:02:2C:79:CC` (*expires on 01/12/2018*) ### 4) Import the GPG key it should have the following fingerprint: `C522 61BE 0A82 3221 D94C A1D1 CB11 CA1D 03FA 5082` ### 5) Download the .iso through torrent or the file, with the signature and verify it by typing in: `gpg --verify Qubes-R3.2-x86_64.iso.asc` ### 6) You can double or triple check it if you are paranoid, and if everything is ok, you can just burn it to a DVD. ### 7) Backup all your important files, and then just install, a clean install of Qubes, this will wipe all your files away, so make sure you have backed them up, or they will be lost. ### 8) Enjoy Qubes! <br/><br/> <CENTER><H1>Getting Started</H1></CENTER> Now at first glance it may look foreign but you will get used to it, here is a very easy series that will teach you how to use it: * https://www.qubes-os.org/video-tours And you find many more videos on Youtube and you can always read the documentation if you have a question: * https://www.qubes-os.org/doc Last but not least Qubes is social, so you can join many social groups: * https://www.reddit.com/r/Qubes * https://www.facebook.com/QubesOS * https://twitter.com/QubesOS * https://www.qubes-os.org/news/ * https://www.qubes-os.org/mailing-lists/ ------------------------------------------ Disclaimer: I am not affiliated with QubesOS. ------------------------------------------ **Sources:** * https://pixabay.com * Qubes logo by [Qubes OS](https://www.qubes-os.org/doc/style-guide/) [GPL](http://www.gnu.org/licenses/gpl.html), via Wikimedia Commons ------------------------------------------- <CENTER><H1>Upvote, ReSteem & <a href="https://steemit.com/@profitgenerator" target='_blank'><img src='https://s4.postimg.org/cfz9b1mnh/bluebutton.png' border='0' alt='bluebutton'/></a></H1> </CENTER>
👍 profitgenerator, ralph-rennoldson, angusleung100, builderofcastles, vanessavi, sellergenius, freebornangel, bitcoinparadise, saamychristen, michaellamden68, niv89, nicolicreer, bmarsh123, gokulnk, lambchop666, hippiepyro, dijital, aismor, me-do, hendrikcrause, vortac, ryan313, dailyfxtrader, walterjay, djleo, fractalnode, rimantas, allyouneedtoknow, rxtro, mightpossibly, domocrypto,