What Is Hashing in Blockchain?
steemhunt·@shadywix·
0.000 HBDWhat Is Hashing in Blockchain?
Hello steemians, I am Shady here and you are welcome to my steemit channel. I’ll be honest with you: despite being a crypto fan for a long time, I’m still a bit uncertain what hashes, hash functions and keys really are. The hash has been described as the “workhorse of modern cryptography” and it is a core element of any blockchain. That’s why in this blog post, I am going to try and break down the hash. Let’s get right into it! 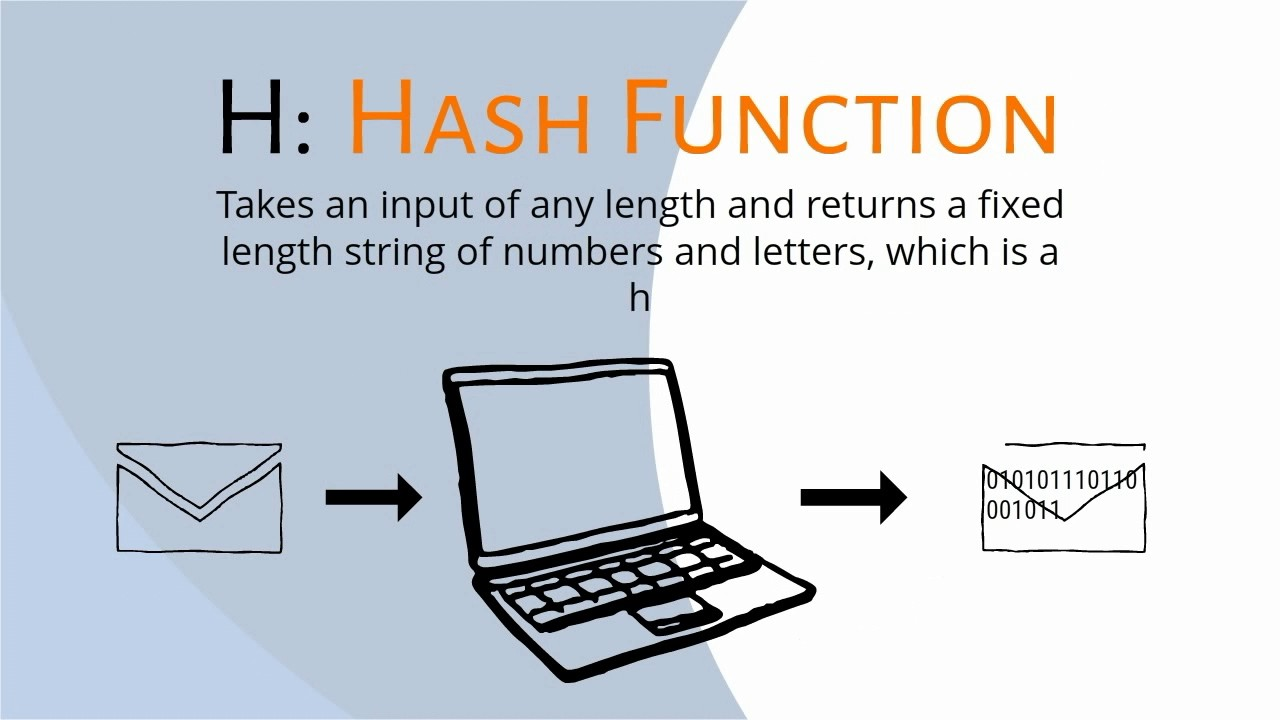 A hash is the output of a hash function, also called a digest. That is because, it is the result of a computation. The computation follows the rules of a hash function. A hash operate takes in a very worth of impulsive size. No matter if it’s a single word or a whole page of text, the function computes an OUTPUT of a fixed size. So, all outputs are equally long no matter the inputs. One very simple hash function is the average checksum. Imagine splitting any number up into single characters. So, for 48 it’s 4 and 8. Then you take the average of these numbers, in this case, 4+8/2 = 6. If you take 1000 and use the same function, the hash is 0.25. That way, you always get a hash between 0 and 10 for any input. This idea helps compare files, compress movies and use blockchains. There are a lot of different hash functions for different use cases. For cryptography, we use cryptographic hash functions. The most well-known cryptographic hash function is SHA-256. What are the main characteristics of a hash function? 1) It needs to be deterministic. The same input needs to generate the same output, like SHA-256 or the function we’ve shown before. 2) It needs to be quick. Because hashing happens so often it should be quick. Today we have no issues producing fast hash functions. 3) It must work one way only. The input can generate the output, but given the output, one must not be able to generate the input. This is a special feature of cryptographic hash functions. So our previous example cannot fulfil this demand, because given an output of 5, I know that 55 is a possible input. In cryptography, this means I have broken the code. For a computer, it is theoretically possible to reverse the input, however, the longer hash you have, the harder it becomes to becomes to solve it. 4) A small change in the input must change the output massively. Even after a minor change in the input, two outputs would look completely different. In this example our little hash function also fails. If I change 888 to 889 the output changes from 8.0 to 8.3. It matters because otherwise breaking the hash is too easy. The SHA-256 function satisfies this criterion: For example: “Dog” yields this: but “Dig” yields this: 5) It must be infeasible to find two different messages with the same hash. Again, that little hash function we’ve talked before fails here. 5, 55 and 64 all have the same output - 5. This makes breaking the code easier. If there are more correct inputs, your chances of finding the correct one is higher. However, it also can lead to dramatic crashes in systems. 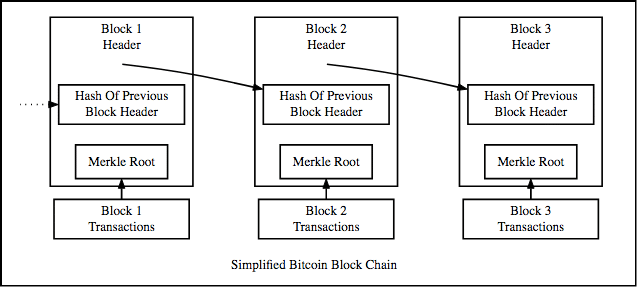 Although, most hash functions are designed to decrease the possibility of two same outputs, it’s still not fully achievable. Why? There is an infinite number of inputs. But the hashing function can only give a finite number of outputs because the length is set. However, we can make it less likely than for example a meteor crashing into Earth. Then we can consider it infeasible, which is all we need for now. Fun fact for conspiracy theorists. The NSA designed the SHA-256 and its variants and some people suspect that they added a backdoor. Backdoors are hidden ways they can use to break the encryption. However, nobody has since found a security flaw or backdoor. Today, 20 years after its initial release SHA-256 is considered safe. Ok, what have we learned today? There are many different types of hashes. Cryptographic hashes are needed for blockchain encryption. Those need to have five properties. They need to be deterministic and fast. They must only work in one way. Reverse engineering must be infeasibly hard. Small changes to the input must change the output massively and collisions must be super rare. Before you go, please note that this content neither represents monetary, legal, or tax advice, neither is it speculated to be understood or understood as solicitation to shop for or sell any securities, coins or tokens. let me know your thoughts in comment section below So thank you so much for reading my blog post please do upvote if you like my content follow me steemit: https://steemit.com/@shadywix twitter: https://twitter.com/ShadyWix?lang=en instagram: https://www.instagram.com/shady_wix/