The Hive Crypto Challenge #1 - Winner Announcement
hive-148441·@timsaid·
0.000 HBDThe Hive Crypto Challenge #1 - Winner Announcement
<center><h1>Prepare - Uncover - Outwit - Find - WIN!</h1>  </center> The 1st HIVE Crypto Challenge is over and we are happy to announce the winner: Congratulations @lefevre! You followed your intuition and stayed on the right track. Solving the puzzle you saved your reward. 500 **HIVE** goes to you. <hr> <center><h1>Solution</h1></center> Here is a breakthrough, showing step by step what you had to do in order to solve the crypto-puzzle. The first two given hints were: <center><h3><br/><br/>Hint Nr.1:</h3> <pre><code>https://hive.blog/hive-174578/@timsaid/timtravels-a-different-kind-of-tree-hint-nr-1 & s/ /D</code></pre><br> and <h3>Hint Nr.2:</h3> <pre><code>197gY7bE</code></pre></center><br> @lefevre took the first right step towards bringing structure into the mesh of hints and found out that the second hint is part of a Pastebin URL. In the post, I wrote the following sentence *"It could also be that some of my hints are trash for the bin"*, which is another reference to Pastebin. <center></center> Opening the pastebin you will see the following message: <center><code>EnCt2f5f470abbd1f510caa1eaecfd1efeb7b9bae72def5f470abbd1f510caa1eaecf5Tg4UK3=1wC i5L3tol7qS/bt1shr3CS/RQNZNt2xlvZ+O6Z2PFk8+Y/0IwEmS</code></center> The string above is a 256-bit AES encrypted message which you need a password to decrypt and read. With the help of @buddyboyb, @lefevre was able to decrypt the message. But how did @buddyboyb know the password? It was hidden within the first hint. <center></center> Inspecting the file URL with regards to the second half of the first hint <code> s/ /D</code> you would extract the following password to decrypt the message <code>cbiikynpp2sigmr</code>. After decrypting the message you will get the following link https://easyupload.io/6d5zo2 which contains a .rar file. Now things will get nasty. The file also contains a password, which is the same as the one for the encrypted message. The .rar file contains three separate files with **NO** instructions. Now comes the title cover into play, on the top you will find a morse code which translates into RAID 4 NO PARITY. <center>  </center> @lefevre obviously knew what he has to do. If you have a look at how [RAID systems](https://en.wikipedia.org/wiki/Standard_RAID_levels) work you would find an idea of how to reconstruct the original file from the given files in the .rar file. He wrote a Python script to put the pieces together: <center> 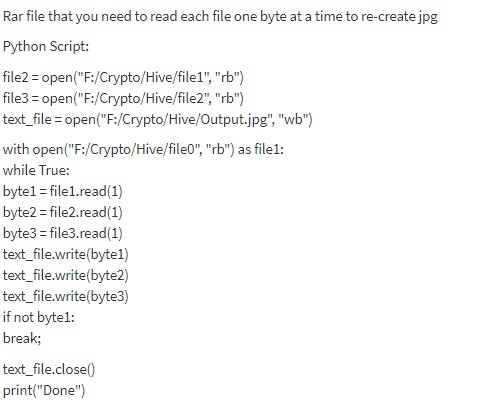</center> The resulting picture and final solution is: <center>https://images.hive.blog/640x0/https://images.hive.blog/DQmdHyFpFnMuC822XgHobL3T2mTSiS7NBBek5u6ZZH9EWqA/output.jpg</center> <hr> Great work and congratulations to the winner and all who participated. Because @bobbyboyb pitched in and helped @lefevre to solve the puzzle, @lefevre transferred him 50 **HIVE**! That's what I call the community spirit! Don't miss the next HIVECrypto Challenge and be prepared. I wish you a great weekend. As for me, I prepare the next challenge and try to make it a little trickier. Thanks again to @innerhive for supporting the contest and contributing with **250 HIVE** to the prize! <hr> Don't forget to check the winners of the MyPictureDay photography contest tomorrow! <br> Yours, Tim
👍 acehnature, alainite, sunshinebear, galione, pixelfan, gerber, nealmcspadden, steemcityrewards, deathwing, emrebeyler, curx, watchlist, roleerob, pataty69, cadawg, mindtrap, bestboom, freddio, gallerani, dlike, triptolemus, determine, permaculturedude, steem.leo, freddio.sport, asteroids, leo.syndication, one.life, maxuvd, someguy123, dappcoder, goodreader, staryao, huaren.news, aivote, ebargains, lordneroo, eliel, improv, furious-one, runicar, rafalski, stinawog, ofildutemps, sustainablelivin, steem.services, nateaguila, flyingbolt, smileyboy, the.curator, mys, aicurator, ratel, heidimarie, delabo, gerbo, discernente, frankk, anacristinasilva, whd, raili, dado13btc, pardeepkumar, fbslo, espoem, ocupation, enjoyinglife, florenceboens, milaan, sacrosanct, bbb2020, themarkymark, karja, gholsa, abcor, buildawhale, upmyvote, ipromote, netaterra, worldfinances, therealyme, coinmarketcal, botante, arcange, gavvet, lays, putu300, kiligirl, hanshotfirst, johannvdwalt, sportspodium, africaunited, ngos, sme, smawkward, brightideas, kirstieclutte, techslut, thatindianlady, raphaelle, timsaid, mafaldation, ralph-rennoldson, experiment, ibringawareness, roswellrockman, alexanderrigov, vampyre.cash, plankton.bot, ace108, bergelmirsenpai, yestermorrow, hyborian-strain, nanzo-scoop, sirdeza, sivehead, i-c-e, mummyimperfect, ak2020, emily-cook, t-bot, mafeeva, fitat40, scoopstakes, nanzo-snaps, goodcontentbot, bigmoneyman, steemlondon, teammo, dylanhobalart, romanaround, bargolis, vidafitnessfeliz, travelingmercies, tanvirrahman, gardeningabc, liberviarum, istillrise, fuzzythumb, dream.trip, dilimunanzar, blocktrades, tomatom, mr-critic.aaa, offgridlife, diamond-head, bue, jlufer, stayoutoftherz, rocksg, sanjeevm, ttg, czechglobalhosts, piotr42, onlavu, varunpinto, kpine, cultus-forex, maryincryptoland, ubongj, kristenantai01, defcon007, skillz, karpnado, pqlenator, bonzopoe, apprentice001, lamorada, goumao, wf9877, daring-celt, diosaerys, superhardness, white-star, satari, daio, yoogyart, melissaofficial, evildeathcore, jphamer1, biggypauls, murathe, transitoria01, bluenarcolepsy, sholi, the-reef, arabisouri, ahmedsy, mrsyria, afrozhive,